VMware heeft versie 6.0.3 build 80004 van zijn virtualisatiesoftware Workstation uitgebracht. Dit pakket doet zijn werk onder Linux of Windows en is in staat om via een virtuele machine diverse besturingssystemen op de hostcomputer te laten draaien. Voor de gastcomputer kan je gebruikmaken van verschillende BSD-varianten, diverse Linux-distributies, Solaris en Windows. Voor meer informatie verwijzen we jullie door naar deze pagina en deze handleiding in pdf-formaat.
Maandelijks archief: maart 2008
VMware Server 1.0.5 build 80187
Vmware heeft een nieuwe versie van Vmware Server beschikbaar gesteld. Het programma is aangekomen bij versienummer 1.0.5 build 80187 en kan vanaf deze pagina voor Windows en Linux gedownload worden. Vmware Server is een virtualisatieprogramma voor servers waarmee meerdere en verschillende besturingssystemen in een virtuele omgeving gedraaid kunnen worden. Meer informatie over dit programma kan op de website gevonden worden. De ontwikkelaars hebben in Vmware Server 1.05 de volgende veranderingen doorgevoerd:
Security Issues Resolved in VMware Server 1.0.5
- A security vulnerability in OpenSSL 0.9.7j could make it possible to forge a RSA key signature. VMware Server 1.0.5 upgrades OpenSSL to version 0.9.7l to avoid this vulnerability. bug 216497), RSA Signature Forgery (CVE-2006-4339)
- An internal security audit determined that a malicious user could attain and exploit LocalSystem privileges by causing the authd process to connect to a named pipe that is opened and controlled by the malicious user. In this situation, the malicious user could successfully impersonate authd and attain privileges under which authd is executing. bug 235420, (Foundstone CODE-BUG-H-001)
- An internal security audit determined that a malicious user could exploit an insecurely created named pipe object to escalate priviliges or create a denial-of-service attack. bug 235833, (Foundstone CODE-BUG-H-002)
- This release updates the libpng library to version 1.2.22 to remove various security vulnerabilities. bug 237049
- A vulnerability in VMware Workstation running on Windows allowed complete access to the host’s file system from a guest machine. This access included the ability to create and modify executable files in sensitive locations. bug 240000, (CORE-2007-0930)
- The authd process read and honored the vmx.fullpath variable in the user-writable file config.ini, creating a security vulnerability. bug 241648
- The config.ini file could be modified by non-administrator to change the VMX launch path. This created a vulnerability that could be exploited to escalate a user’s privileges. bug 241677
In addition, Version 1.0.5 improves Remote Console performance and screen refreshing.
| Website | Vmware |
|---|---|
| Download | http://register.vmware.com/content/download.html |
VMware Player 2.0.3 build 80004
Het virtualisatieprogramma Vmware Player heeft een upgrade naar versie 2.0.3 gekregen. De nieuwe versie kan voor Windows en Linux gedownload worden nadat deze pagina ingevuld is. Met behulp van Vmware Player is het mogelijk om virtual machines te draaien die gemaakt zijn via Vmware Workstation, Vmware Server en Vmware ESX Server. Ook worden virtual machines van Microsoft en Symantec LiveState Recovery ondersteund.
VMware Player 2.0.3 addresses the following security issues:
- On Windows hosts, if you have configured and enabled a shared folder, it is possible for an attacker to write arbitrary content from a guest system to arbitrary locations on the host system (CORE-2007-0930). (bug 200360)
- This release updates the libpng library to version 1.2.22 to remove various security vulnerabilities. (bug 224453)
| Website | Vmware |
|---|---|
| Download | http://www.vmware.com/download/player/player_reg.html |
GW7 SP3, GW65 SP6 update 3
GW7 SP3 and GW65 SP6 update 3 are out.
GroupWise 7 SP3 Windows and NLM US and MULTI 703
GroupWise 7 SP3 Linux Full US and MULTI 703
GroupWise 7 SP3 Windows Client US and MULTI 703
GroupWise 7 SP3 Linux Client US and MULTI 703
GroupWise 7 SP3 Mac Client US and Multi 703
GroupWise 6.5.6 Update 3 Windows client 656up3
Read Dean Lythgoe’s blog on this SP.
About the security issue :
Description:
A security vulnerability exists in the GroupWise Windows client API that can allow programmatic access to non-authorized email under certain conditions. The attacker must first authenticate to GroupWise and be a recipient of a shared folder from another user. The attacker could then exploit the vulnerability to gain unauthorized access to non-shared email in the mailbox of the sharer.
Cause: An unspecified error in the Windows client API
Workaround:
Users that have shared folders with other users can protect their email by removing shared access until remedial steps have been completed. It is not necessary to delete the contents of the shared folders and they can be re-shared after the administrator has locked out older client versions.
To remove shared access to a folder select the shared folder, click File > Sharing, then select Not shared.
Remedy:
For GroupWise 7 – Customers running GroupWise 7.0 clients
should immediately upgrade all clients to GroupWise 7 SP3 (dated 09 Mar 2008) and lock out older clients via ConsoleOne.
GroupWise 6.5 Windows – Customers running GroupWise 6.5 Windows clients should immediately upgrade all Windows clients to the GroupWise 6.5 SP6 client Update 3 (dated 11 Mar 2008), or upgrade to GroupWise 7 SP3. Older clients must be locked out via ConsoleOne.
GroupWise 6.5 Linux – Customers running GroupWise 6.5 Linux or Mac clients should immediately upgrade to GroupWise 7 SP3 (dated 09 Mar 2008).
For GroupWise 6.0 and previous – Customers still running unsupported GroupWise client versions (5.x and 6) should immediately upgrade clients and servers to either GroupWise 6.5 SP6 Update 3 or to GroupWise 7 SP3. Older clients must be locked out via ConsoleOne.
If Blackberry Enterprise Server (BES) is installed in a GroupWise 7 environment then upgrade the BES to a version which supports the GroupWise 7 client (BES 4.0 SP 7 or BES 4.1 SP4), and upgrade the GW client installed on the machine to 7.0 SP3 (dated 09 Mar 2008).
If Blackberry Enterprise Server (BES) is installed in a GroupWise 6.5 environment then upgrade the GW client installed on the machine to 6.5 SP6 Client Update 3 (dated 11 Mar 2008).
Special Instructions and Notes:
For instructions on locking out older client versions please refer to GroupWise documentation for your GroupWise version:
GroupWise 7: http://www.novell.com/documentation/gw7/gw7_admin/index.html?page=/documentation/gw7/gw7_admin/data/adqaf1n.html
GroupWise 6.5: http://www.novell.com/documentation/gw65/index.html?page=/documentation/gw65/gw65_admin/data/adqaf1n.html
If running a mixed environment of 6.5 and 7.0 clients then make sure to lock out based on client release date rather than client version. The recommended date should be 08 Mar 2008 in order to ensure the system is not vulnerable.
RIM BES 4.1 SP5 for GroupWise
Posted by Jay Parker (NTS) in the NGW List :
I pinged my contacts at RIM and got the following info.
During the last GWAVA one of the presenters from RIM communicated that RIM is targeting SP5 for mid-year. It will include HTML and email rendering support along with some additional features. RIM is targeting feature parity with other platforms around the same time.
In email my RIM contact also mentioned that SP5 for the other platforms has not yet officially shipped. So now that BES for GroupWise 4.1.4 has shipped, all platforms are at the same SP level (at least for a little while). This seems to be confirmed by the link <…> provided from RIM which says that SP5 is “Coming Soonâ€.
I agree that it’s not good that BES SPs for GroupWise ship behind the Exchange SPs. In RIM’s defense I’ll state that we’re pushing them very hard to move their architecture away from the client API to SOAP. And as they make incremental steps to this effect with each release it can introduce bugs which cause delays.
We work very close with their dev team. From my interactions with that team and other contacts at RIM, I’m convinced they have a very talented and committed team working on GroupWise. I think you’ll see improvement in quality with each release as well as Exchange SP vs. GroupWise SP availability window shorten.
GNOME 2.22 released
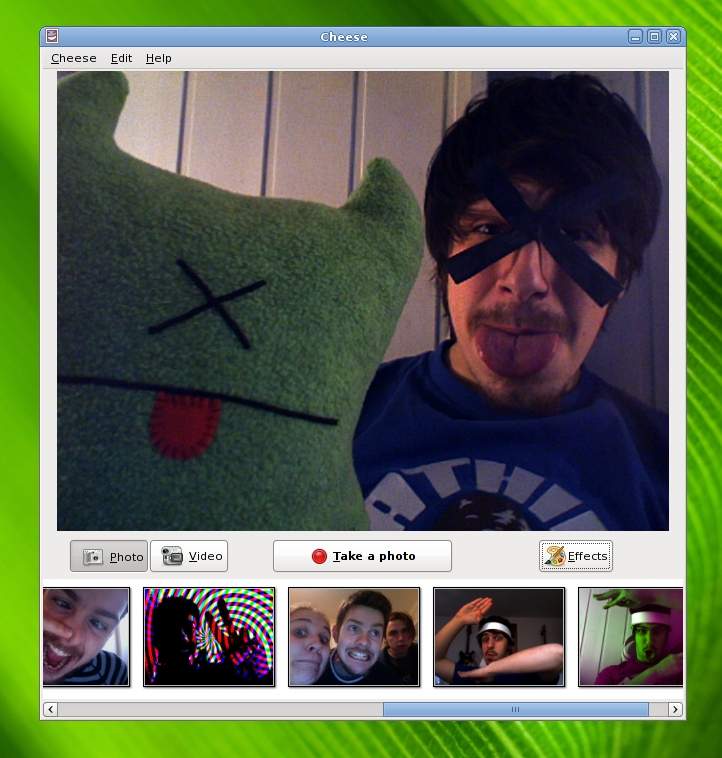
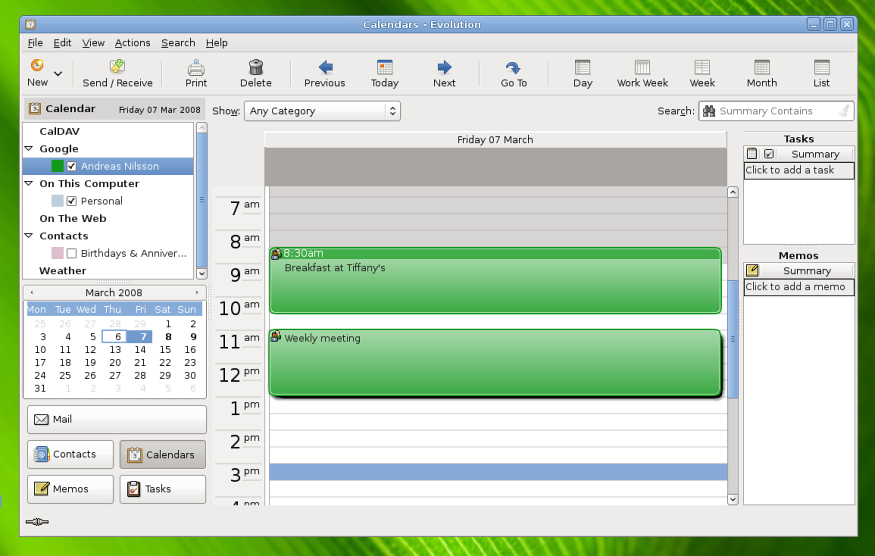
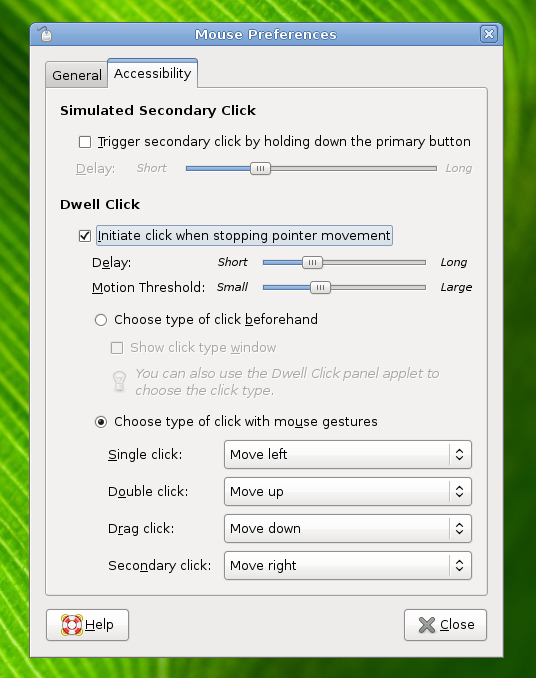
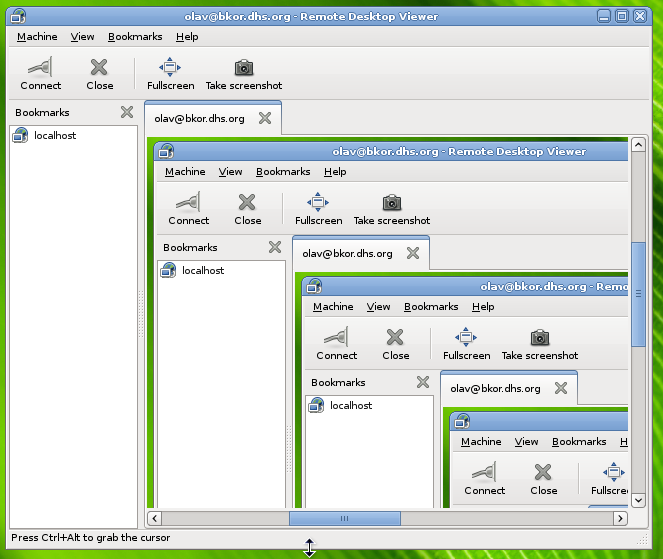
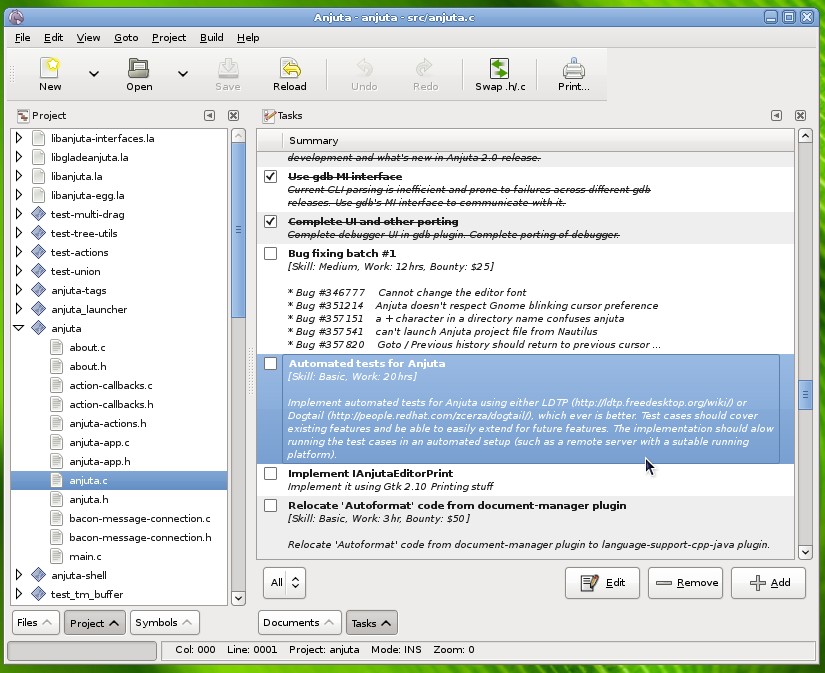
 De ontwikkelaars van Gnome hebben woensdag versie 2.22 van de desktopmanager uitgebracht. Nieuw in Gnome 2.22 zijn onder andere de applicaties Cheese en Anjuta. Cheese is een programma waarmee foto’s en video’s met een webcam gemaakt kunnen worden. Anjuta is een integrated development environment voor het kloppen van code in C en C++. Daarnaast zijn er nieuwe tools voor systeembeheerders is versie 2.22 gestopt en is de e-mailclient Evolution onder handen genomen. Wat er nog meer veranderd is in Gnome 2.22 kan in dit nieuwsbericht gelezen worden.
De ontwikkelaars van Gnome hebben woensdag versie 2.22 van de desktopmanager uitgebracht. Nieuw in Gnome 2.22 zijn onder andere de applicaties Cheese en Anjuta. Cheese is een programma waarmee foto’s en video’s met een webcam gemaakt kunnen worden. Anjuta is een integrated development environment voor het kloppen van code in C en C++. Daarnaast zijn er nieuwe tools voor systeembeheerders is versie 2.22 gestopt en is de e-mailclient Evolution onder handen genomen. Wat er nog meer veranderd is in Gnome 2.22 kan in dit nieuwsbericht gelezen worden.
Today, the GNOME Project celebrates the release of GNOME 2.22, the latest version of the popular, multi-platform free desktop environment and of its developer platform. Released on schedule, to the day, GNOME 2.22 builds on top of a long series of successful six months releases to offer the best experience to users and developers.
For more than 10 years now, the project has been seeing a tremendous amount of work. And as usual, it’s hard to come back to a previous version of GNOME once you’ve tried GNOME 2.22, which is probably the best compliment the project can receive.
This six months effort wouldn’t have been possible without the whole GNOME community, made of contributors from all around the world: hackers, documentors, usability and accessibility specialists, translators, maintainers, sysadmins, companies, artists, users and testers. GNOME would not exist without all those people. Thanks very much to every one of them!
| Website | Gnome |
|---|---|
| Download | http://library.gnome.org/misc/release-notes/2.22/#rninstall… |
Monitor Linux POA and MTA Logs
Check out this great free tool from Tay Kratzer, mr. GroupWise on Linux !
He’s whipped up an application that can help you when trying to monitor GroupWise POA and GroupWise MTA logs on the Linux platform.
You can freely distribute this software.
I’ve listed this tool on GWCheck.com in the TOOLS – Admin GW – Linux menu.

